IP addresses in Bitcoin transactions identifiable, study finds
In a new study, researchers from the University of Luxembourg have shown that it is feasible to reveal the IP address behind every Bitcoin transaction, with the help of only a few computers and approximately €1,500, according to a university article.
Researchers at the university’s Laboratory of Algorithms, Cryptology and Security found that Bitcoin does not protect a user’s IP address and that it can be connected to the user’s transactions in real time. To discover this, a hacker would need only a few computers and approximately €1,500 a month for server and traffic expenses. The Register reported that according to the study, this should be enough to begin identifying users’ IP addresses with as much as 60 percent accuracy. If attackers needed to be more stealthy, their success rate would fall to 11 percent.
In what they call “a generic method to deanonymise a significant fraction of Bitcoin users and correlate their pseudonyms with public IP addresses,” the researchers state that clients can be uniquely identified by their “entry nodes,” and that these identify the transaction origin, reported The Register.
“In a concrete example, an attacker with a few GB of storage and no more than 50 connections to each Bitcoin server can disclose the sender’s IP address in 11 per cent of all transactions generated in the Bitcoin network,” claimed the paper, which was recently presented at an Association of Computing Machinery conference.
The methods are said to work for “the most common and the most challenging scenario when users are behind NATs [network address translation] or firewalls of their ISPs” delivering the ability to “link transactions of a user behind a NAT and to distinguish connections and transactions of different users behind the same NAT,” according to the researchers, as reported by Silicon Angle.
Silicon Angle said the study described the four steps in the process:
- Getting the list of servers, which is regularly refreshed.
- Create a list of Bitcoin users for deanonymization.
- Learning entry nodes from users from when they connect to the network.
- Listening to servers and mapping transactions to entry notes and then to users.
According to The Register, the study noted that Tor, the popular anonymization network, would protect this, but that can be defeated as well should the attacker be willing to take a risk: Bitcoin servers can be barred from accepting Tor connections, but declining those connections would be noticed.
The researchers present methods to prevent attacks on users’ privacy, including preventing Tor blacklisting and blurring the connectivity footprint, reported Silicon Angle.
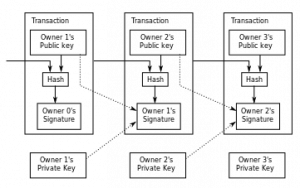
Image: Public domain image by Graingert










Is this the same for users exclusively relying on VPN tunnels ?